How Social Engineering Puts User Data at Risk
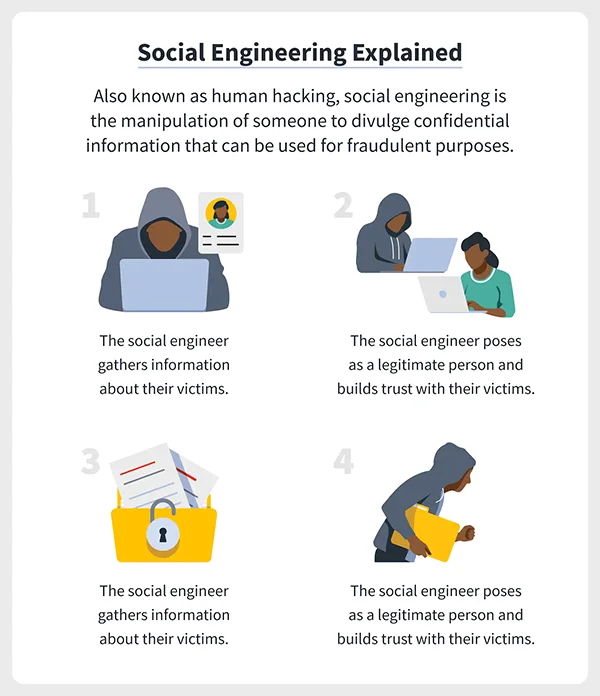
Social engineering is a manipulation tactic used to obtain sensitive information from users to get access to resources, accounts, or extremely private details.
The practice is termed as such since it requires some effort to psychologically trick someone into sharing certain types of information.
In comparison, hacking is a straightforward way of deceiving users, but social engineering is a little more nuanced as it involves a lot of psychology and maneuvering.
It also takes more effort than hacking since scammers spend some time setting the premise for the same trap.
People may be wary of hackers and careful about not sharing their passwords. But because it is easy to replicate official emails or pretend to be somebody else, a lot of people are victims of social engineering.
This article explores the strategies applied to social engineering theft and how customers can become aware and prevent the loss of their personal and professional information.
Types of Social Engineering Methods
Protecting our reports and content cannot be neglected in this digitally progressive world. It just takes a year when another advanced tech enters the market.
This triggers the hackers to make easy money through manipulative tactics. There are multiple ways in which social engineering puts user data at risk.
1) Phishing
Phishing involves adding a malicious link or an attachment to an email or a text which is the most common method of social engineering.
Regardless of how careful one wants to remain; curiosity gets the best of humans who then cave in and click on the link and attachment in the end.
These can easily pick up information from people’s devices and give free access to hackers.
Users can very easily protect themselves from phishing by carefully reading the contents of the email or text message sent to them and mindfully looking at the sender.
Texts specifically meant for phishing can be easily identified.
FAST FACT
95% of attacks on business networks are the result of successful spear phishing.
2) Spear-phishing
This is a way of phishing that involves more personalized messages and can take a long time to be successful.
It entails a lot of planning and dedication since the hacker has to play along to gain someone’s trust.
Personalized emails are sent to certain targeted people to get access to their information.
Recipients can then be fooled through attachments containing malicious spyware, and links that can record their data.
Or can even be directly asked to share certain information with the excuse that the safety of their files must disclose a few relevant details.
3) Pretexting
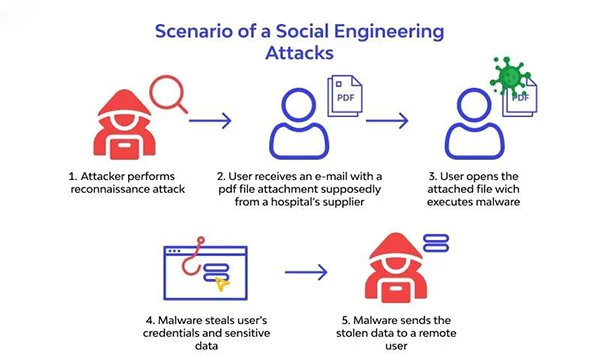
This is a way of social engineering that sets the premise for the attack on sensitive data. Scammers do this by pretending to be someone users can trust.
They can impersonate bank employees or customer service representatives and act like they are there to support them through some sort of malfunction.
- Scammers looking for bank details will claim that the user’s debit or credit card has been temporarily blocked.
- They further blackmail that it can only be opened if they disclose the PIN. Any unsuspecting customer may mindlessly give out this information.
- Similarly, anybody pretending to be a customer service representative will claim that the user’s device will shut down if they do not share the password on a phone call.
This is another way in which user’s data is easily obtained through inciting fear of losing valuable info.
4) Baiting
Users who indulge in the piracy of movies, shows or even music are more susceptible to clickbaits.
Anybody using a website that is not secure and contains ads is full of clickbaits which makes it tempting for people to click on random links since they are promised exciting content.
They are lured in by offers such as that of a free movie without any ads or music without any interruption.
Those who want to steer clear of subscriptions pick such alluring offers and end up caving.
By clicking unknown links, they can either accidentally download malware into their device or simply get their reports stolen.
This is another way for attackers to get into somebody’s system and gain access to sensitive information.
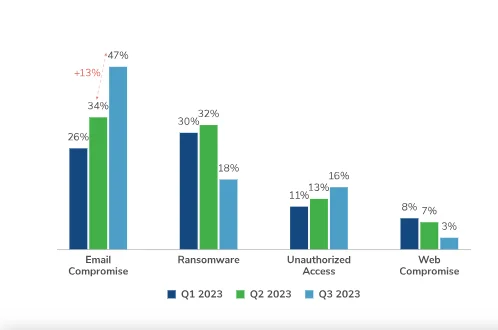
The graph below shows that victims of cyberattacks were most likely manipulated through email compromise as compared to ransomware, unauthorized access, and web infiltration.
5) Tailgating
This may be a less common way of internet theft and may be heavily portrayed in movies but tailgating is a method of getting hold of sensitive data physically.
Businesses and office premises must be secured to keep outsiders at bay and prevent them from entering at all times.
However, there may be security breaches if the right measures are not taken immediately and therefore regular maintenance checks are recommended.
Data that is stored in physical copies can be easily removed from these places. Devices can also be very easily stolen if they are physically accessible.
For this reason, IT asset management is significant since companies can keep track of where their assets are and who last had them.

6) Social Media Feeds
This is a lesser-known way of social engineering but scammers have come up with a new way of luring people into sharing personal details.
- Not everyone will identify this since it is covertly done and is portrayed as a harmless way to pass the time and indulge in innocuous “oversharing”.
- Application users will be encouraged to come up with “band names” or “stage names” by putting the name of their first pet with their middle name to see what name would be formed.
- These answers are mostly used for security questions in case somebody has forgotten their password.
- Enticing app users to comment under posts with these answers is easy since people like being active online.
Online thefts can be prevented in multiple ways by spreading awareness online and educating about various online thefts.
- Users should be mindful and vigilant while checking emails, visiting random websites, and engaging with posts on Instagram or Facebook.
- In this way, they can very easily protect themselves from breaches of personal data and information.
- They should filter out emails that seem suspicious and never download an attachment they do not trust.
- They should use multifactor authentication to add an extra layer of security.
- Their devices should be protected with antivirus software to ensure that no viruses do not allow any attackers to access their data.
Conclusion
Social engineering is one of the processes that lead to the breach of data and privacy.
It takes more effort than hacking since attackers must be creative with fooling users into giving out their information.
It involves more steps and requires a lot of planning to identify ways in which internet breaches are possible.
A lot of times, attackers have to gain the trust of users to penetrate their content and easily use it. Once trust has been earned, it is easy to obtain the data.
Social engineering is not restricted to online activities but can also be applied in real life if somebody physically wants to steal information or devices containing data.
Share