Spotting Dangerous Emails: 5 Practical Tips
As of 2022, global email users were over 4.2 billion, still, like all digital methods of communication, they are potential tools of deceit. They are also just as vulnerable to cyber threats as the others.
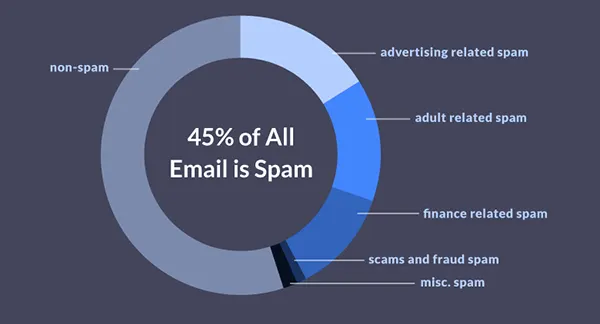
Email scams are becoming too common and catch people in the trap every single time even though they are aware of it. Consequently, everyone needs to practice caution when dealing with these.
To protect yourself from these threats, here are five detailed tips to implement said caution and secure your email. Read on to learn more about it!
Keep Track of Expected Emails
Harmful emails need hooks to lure individuals because their issue would imply attention-grabbing information like urgent problems, potential discounts, job offers, etc.
The best way to ignore the emotions invoked by suspicious activities like these is to have a list of expected messages. An email that isn’t a newsletter or promotion, thus, stands out and demands careful consideration.
However, ruling an electronic mail as illegitimate based only on the topic could be costly, which creates the need to assess the body of the content as well.
Below are some considerations worth remembering:
- Any entity asking directly for Personal Identifying Information or sensitive information is suspicious. Legitimate companies consider the security of customers when requesting private information online, so, they are unlikely to make a direct request.
- Emails containing sensitive information like usernames in their subject or body are suspicious.
- Expected notifications can also be treacherous because man-in-the-middle schemes and BEC scams mostly operate within such message correspondence that can be solved by using strong, unique passwords.
Also, emphasize their need within your company or private network. If there is a need for many such passwords, consider a password manager to ease the mental burden.
Confirm the Sender’s Information
Sometimes, the smoking gun in a malicious email isn’t in the subject or body, instead, it is in the sender’s details. A risky message may come from an unknown address or one designed to mimic a trusted address.
Before opening an electronic mail from a seemingly trustworthy address, double-check with the source via another means of communication.
Compare the email address to that of past correspondence because there might be inconsistencies in the characters within.
Messages from unknown sources are trickier, and a Google or social media search can clarify a sender’s identity.
You can also confirm the source’s legitimacy through mutual connections if any exist. In the absence of such confirmation, an expected email, or a relevant subject, ignore it.
Did You Know?
The first spam message email was sent in 1978.
Utilize a VPN for Enhanced Security
While focusing on email content and source legitimacy is vital, enhancing your network safety is equally necessary. Utilizing a VPN can add a layer of protection.
A VPN, or Virtual Private Network, encrypts your internet connection, making it more difficult for hackers to intercept or access your online activities, including online mail communications.
This is especially useful when accessing electronic mail over public Wi-Fi networks, which are often less secure and more susceptible to cyber threats.
A VPN protects you from threats and blocks malware by routing your internet connection through a secure, encrypted tunnel. Your sensitive information remains private and safe from potential eavesdroppers.
Check for Contact Details
The presence of contact information only supports the legitimacy of corporate email messages. Such emails, or those of an associated representative, likely have relevant contact addresses.
The absence of these details from a corporate message like that should trigger suspicion. You can compare it to past correspondence for confirmation in such a case.
If it lacks information and contains directives, it is not worth following, ignore the mail and get in touch with the company via a new one (using the relevant subject, and don’t forget to delete it.
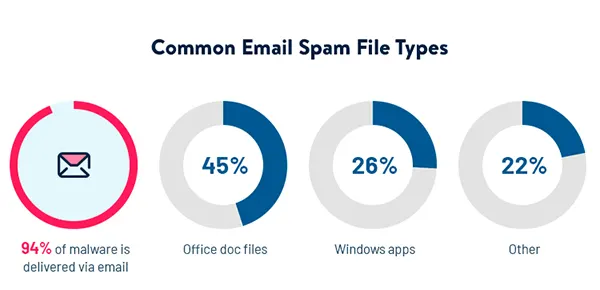
Beware of Unexpected Attachments or Links
The bread and butter of email phishing scams lies in attachments and links that are sent while sharing sensitive files. So, how do we identify the dangerous ones?
Email services generally have systems in place to identify and filter harmful messages or links. However, without invading your privacy (unless permitted by you), there’s a limit to what they can do.
Here are some tips to help navigate attachments and links:
- Normalize ignoring any attachments in unexpected emails that are especially pertinent if the attachment possesses a .exe extension. An unexpected executable file is a huge red flag.
If it originates from a trusted associate, seek clarity before downloading the attachment.
- Don’t open links from an unknown account, no matter how innocuous they seem. Check the sender’s information, the body of the email, etc.
If all checks out, hover your mouse icon over the link to see the URL. You can then verify the access path and domain name before clicking.
- If the clicked link leads to a downloadable file, cancel the download or if it leads directly to a page requesting information, ignore the prompts until you can confirm the site.
A respectable business outfit would not provide or request information in such ways.
Conclusion

The above tips are adequate for securing personal email accounts and being safe from the looming hackers. However, the cybersecurity needs of corporate networks require more.
In other words, email safety tools and solutions guarantee your mailing safety as personal or corporate enterprise solutions.
Share